The Ultimate Online Privacy Guide in 2025
Transparency First: This post contains affiliate links. If you make a purchase through these links, we may earn a commission at no extra cost to you. Our recommendations are always based on our own research and opinion. Please read our full for more info.
Every time you send an email, search for a recipe, or scroll through social media, you leave behind a trail of digital breadcrumbs. Your data is constantly being collected, analyzed, and often sold, creating a detailed profile of your habits, interests, and personal life. While it’s easy to feel powerless against this vast data collection machine, the truth is you have more control than you think.
Protecting your online privacy isn’t about becoming an invisible cyber-ninja overnight. It’s about taking a series of small, manageable steps to build layers of protection, making yourself a much harder target for trackers, advertisers, and malicious actors.
This online privacy guide is designed for everyone, from the complete beginner to those who are already privacy-conscious. We’ll walk you through ten actionable steps you can take right now to significantly improve your digital privacy and take back control of your personal information.
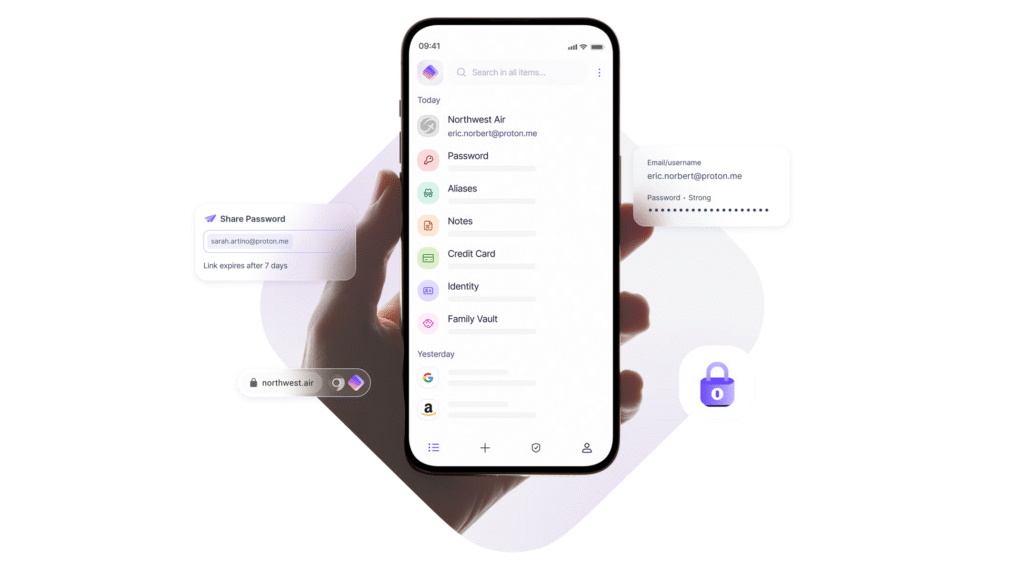
1. Master Your Passwords with a Password Manager
The single most common point of failure in digital security is a weak or reused password. If you use the same password for your email, social media, and online banking, a breach at one service can compromise your entire digital life.
The solution is simple: use a strong, unique password for every single online account. But how can you possibly remember dozens of complex passwords like 8$z@pW!qR#t2*fG? You don’t have to.
A password manager is a secure digital vault that creates, stores, and autofills your passwords for you. You only need to remember one strong “master password” to unlock the vault.
Actionable Steps:
- Choose a reputable password manager: Services like Proton Pass, Bitwarden, or 1Password are excellent choices. They use zero-knowledge encryption, meaning even the company itself cannot access your stored passwords.
- Generate strong passwords: Let the password manager generate long (16+ characters), random passwords for all your accounts.
- Conduct a password audit: Go through your most important accounts (email, banking, social media) and update them with new, unique passwords generated by your manager.
2. Enable Two-Factor Authentication (2FA) Everywhere
Two-Factor Authentication (2FA) is one of the most powerful security measures you can enable. It adds a second layer of security to your accounts, requiring not just something you know (your password), but also something you have (your phone or a security key).
Even if a hacker steals your password, they won’t be able to log in without that second factor.
Actionable Steps:
- Use an authenticator app: While SMS-based 2FA is better than nothing, it can be vulnerable to SIM-swapping attacks. A more secure method is to use an authenticator app like Aegis Authenticator or Ente Auth.
- Enable 2FA on critical accounts: Prioritize your email, financial accounts, social media, and password manager. Go into the security settings of each service and follow the instructions to enable 2FA.
3. Reclaim Your Browsing with a Privacy-Focused Browser
The browser you use is your main window to the internet, and popular choices like Google Chrome are notorious for tracking your every move to fuel their advertising business. Switching to a privacy-focused browser is a simple change with a huge impact.
Actionable Steps:
- Switch your default browser:
- Brave: An excellent choice that blocks ads and trackers by default, making it fast and private out of the box.
- Firefox: A powerful open-source browser from Mozilla. When paired with privacy extensions, it’s a fantastic alternative.
- Install essential privacy extensions: If you stick with Firefox (or even a Chromium-based browser), install these two extensions immediately:
- uBlock Origin: The gold standard for blocking ads and malicious scripts.
- Privacy Badger: Developed by the Electronic Frontier Foundation (EFF), it specifically blocks invisible trackers that follow you across websites.

4. Use a Private Search Engine
Every search you make on Google is logged, stored, and used to build a profile about you. To break free from this surveillance, switch to a search engine that doesn’t track you.
Actionable Steps:
- Change your default search engine:
- DuckDuckGo: The most well-known private search engine. It doesn’t store your search history or IP address and gets its results from sources like Bing without sharing any of your personal information with them.
- Startpage: This service provides you with Google’s search results but acts as a private intermediary. Startpage submits your query to Google and returns the results to you, so Google never sees who you are.
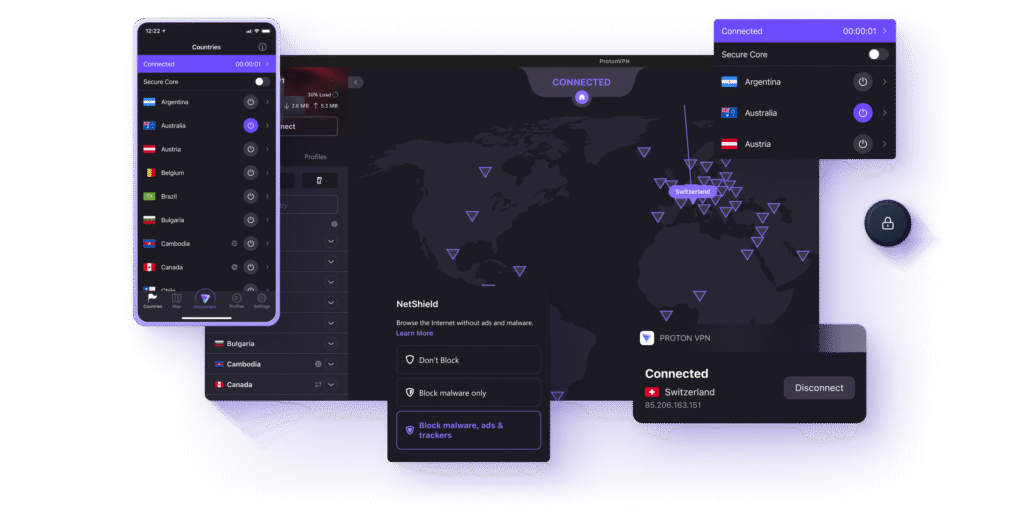
5. Encrypt Your Connection with a VPN
A Virtual Private Network (VPN) is an essential tool for modern online privacy. It creates an encrypted “tunnel” for your internet traffic, hiding your online activity from your Internet Service Provider (ISP), public Wi-Fi snoops, and other third parties. It also masks your real IP address, making it appear as if you’re browsing from the VPN server’s location.
Actionable Steps:
- Choose a trustworthy VPN: Avoid “free” VPNs, as they often make money by selling your data. Opt for a reputable, paid service with a strict no-logs policy that has been independently audited. Proton is a highly respected provider based in privacy-friendly Switzerland, known for its strong security features and audited no-logs policy.
- Use a VPN on public Wi-Fi: This is non-negotiable. Public Wi-Fi networks (at cafes, airports, hotels) are notoriously insecure. A VPN encrypts your connection, protecting you from hackers on the same network.
- Use a VPN at home: Your ISP can see every website you visit. A VPN prevents this, giving you back your browsing privacy.
6. Lock Down Your Social Media Accounts
Social media platforms are designed to encourage oversharing. Taking a few minutes to review and tighten your privacy settings can make a massive difference in who sees your personal information.
Actionable Steps:
- Conduct a privacy checkup: Go into the settings of each social media account (Facebook, Instagram, X, etc.) and look for the “Privacy” or “Security” section.
- Set your profile to private: This ensures only approved friends or followers can see your posts.
- Limit who can find you: Restrict searchability by your email address or phone number.
- Be mindful of what you post: Avoid sharing sensitive information like your home address, phone number, or details about your daily routine.
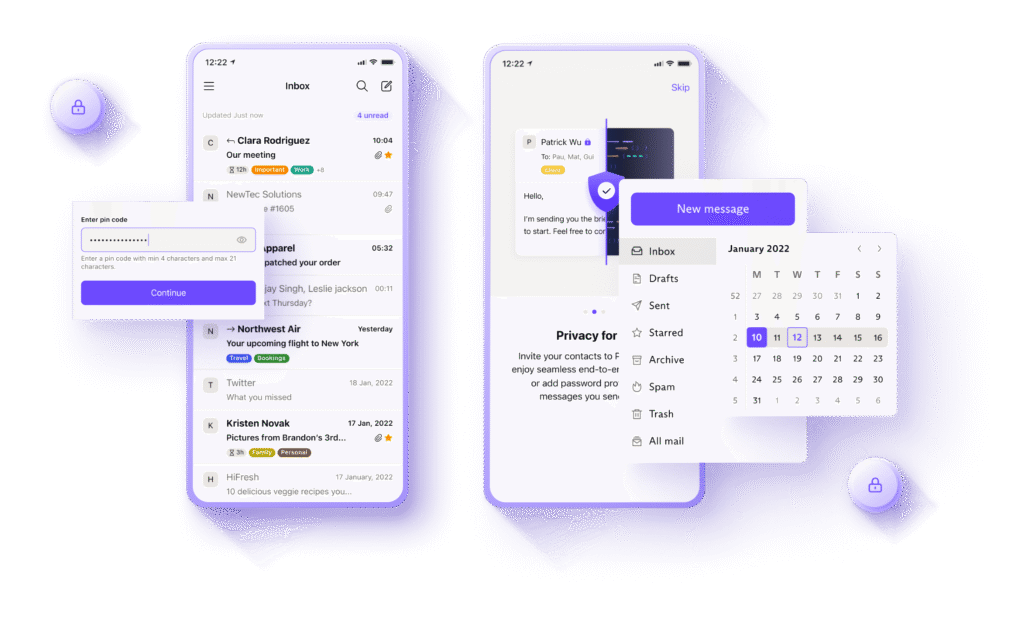
7. Use Encrypted Communication
Standard SMS text messages and many popular messaging apps are not secure. Your mobile carrier can read your texts, and services like Facebook Messenger scan your conversations. For private conversations, use an app that provides end-to-end encryption (E2EE).
E2EE means that only you and the person you’re communicating with can read the messages. Not even the company that runs the service can access them.
Actionable Steps:
- Use Signal: Widely regarded as the gold standard for secure messaging, Signal is free, open-source, and uses robust end-to-end encryption for both messages and calls.
- Use a secure email provider: Standard email services like Gmail scan the contents of your emails for advertising purposes. For sensitive communications, consider a service like Proton Mail, which offers end-to-end encryption and is based in Switzerland, a country with strong privacy laws.
8. Minimize Data Collection on Apps and Services
Many apps and services ask for more permissions than they actually need to function. Regularly reviewing these permissions can limit the amount of data they collect.
Actionable Steps:
- Review app permissions on your phone: On both Android and iOS, go into your settings and review which apps have access to your location, camera, microphone, and contacts. If an app doesn’t need a permission to function, revoke it.
- Use burner email addresses: When signing up for a new service or newsletter you don’t fully trust, use a disposable email alias instead of your primary email. Services like Proton include a feature that generates these aliases for you, protecting your real inbox from spam and data breaches.
9. Keep Your Software and Devices Updated
Software updates aren’t just about new features; they often contain critical security patches that fix vulnerabilities discovered by researchers. Running outdated software is like leaving a window open for hackers.
Actionable Steps:
- Enable automatic updates: On your computer, phone, and browser, turn on automatic updates whenever possible. This ensures you’re always running the latest, most secure version.
- Don’t ignore update prompts: If a device or application prompts you to update, do it as soon as is convenient.
10. Be Vigilant Against Phishing and Social Engineering
The most sophisticated security technology in the world can be defeated if you are tricked into giving away your credentials. Phishing (via email) and smishing (via text message) are attempts to deceive you into clicking a malicious link or revealing personal information.
Actionable Steps:
- Be skeptical of unsolicited messages: If you receive an unexpected email or text from your bank, a delivery service, or a tech company, be suspicious.
- Check the sender’s address: Look closely at the sender’s email address. Scammers often use addresses that are slightly different from the real one (e.g.,
support@paypaI.comwith a capital “i” instead of an “l”). - Never click links directly: Instead of clicking a link in a suspicious email, go directly to the company’s official website by typing the address into your browser and log in there.
Conclusion: Privacy is a Journey, Not a Destination
Taking control of your digital privacy is an ongoing process. Start with one or two steps from this list—like installing a password manager and enabling 2FA—and build from there. Each small change you make adds another layer of protection, collectively creating a strong defense for your digital life.
You have the right to privacy, and you have the power to protect it.

